
At least seven hacking groups are behind a massive surge in ‘TrojanOrders’ attacks targeting Magento 2 websites, exploiting a vulnerability that allows the threat actors to compromise vulnerable servers.
Website security firm Sansec warned that almost 40% of Magento 2 websites are being targeted by the attacks, with hacking groups fighting each other over control of an infected site.
These attacks are being used to inject malicious JavaScript code into an online store’s website that can cause significant business disruption and massive customer credit card theft during a busy Black Friday and Cyber Monday period.
The trend is expected to continue as we head towards Christmas when online shops are at their most critical and simultaneously most vulnerable time.
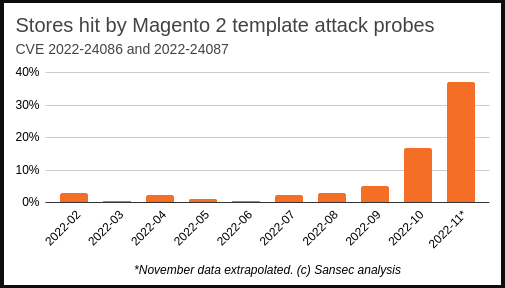
Source: Sansec
The TrojanOrders attack
TrojanOrders is the name of an attack that exploits the critical Magento 2 CVE-2022-24086 vulnerability, allowing unauthenticated attackers to execute code and inject RATs (remote access trojans) on unpatched websites.
Adobe fixed CVE-2022-24086 in February 2022, but Sansec says many Magento sites still need to be patched.
“Sansec estimates that at least a third of all Magento and Adobe Commerce stores have not been patched so far,” explains a new report by eCommerce cybersecurity firm SanSec.
When conducting TrojanOrders attacks, hackers typically create an account on the target website and place an order that contains malicious template code in the name, VAT, or other fields.
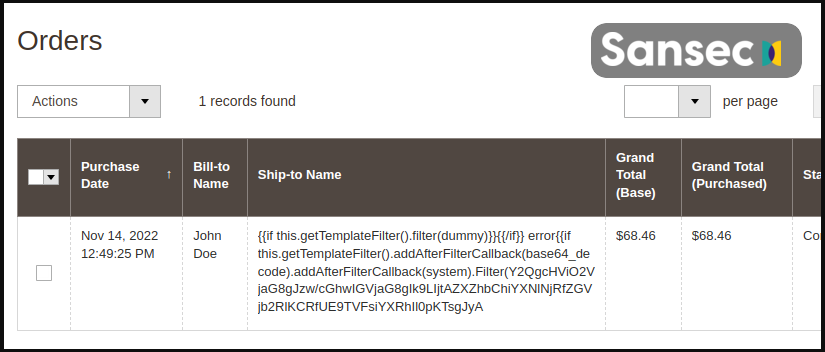
Source: Sansec
For example, the above attack will inject a copy of the ‘health_check.php’ file on the site, containing a PHP backdoor that can run commands sent via POST requests.
After gaining a foothold on the website, the attackers install a remote access trojan to establish permanent access and the ability to perform more intricate actions.
In many cases observed by Sansec, the attackers scanned for the presence of ‘health_check.php’ upon compromise to determine if another hacker had already infected the site, and if so, replace the file with their own backdoor.
The attackers ultimately modify the site to include malicious JavaScript that steals customers’ information and credit card numbers when purchasing products in the store.
Why is there a surge after so long?
Sansec’s analysts believe that there are multiple reasons we are seeing a surge in attacks targeting this vulnerability.
First, a large number of Magento 2 sites remain vulnerable to these attacks, even ten months after the patches became available.
Second, PoC (proof of concept) exploits have been available for a long time, allowing exploit kit authors to incorporate them into their tools and profit by selling them to low-skilled hackers.
These Magento exploits are so abundant they are sold for as low as $2,500, whereas in early 2022, they cost between $20,000 and $30,000.
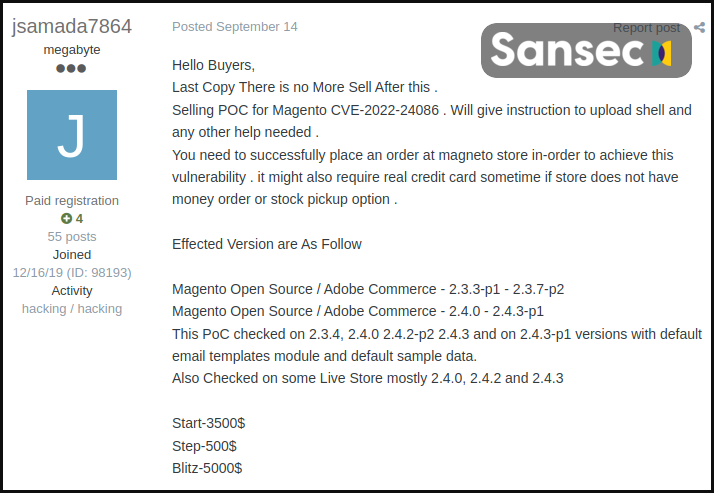
Source: Sansec
Finally, the timing is ideal for these attacks, as websites are seeing increased traffic due to the holiday season, meaning malicious orders and code injections may be more likely to be overlooked.
How to protect your site (and customers)
If you have not applied the security update that addresses CVE-2022-24086, you should do so as soon as possible.
Additionally, scrutinize orders to find signs of a TrojanOrder attack, like template code in order forms or orders submitted by anonymous email accounts using Protonmail, Tutanota, etc.
Finally, use a backend malware scanner to discover potential past infections that have resulted in RAT injections on your site.
Sansec says Magento’s official tool, Security Scan, only scrapes the front end, so it can’t catch TrojanOrders.
For this reason, the security firm offers one month of free access to its scanner to help administrators clean their sites.
Remember, detecting and removing malware and PHP backdoors will only stop future infections if the Magento 2 patches are applied, so this is still the most crucial step to take.
Source: https://www.bleepingcomputer.com/news/security/magento-stores-targeted-in-massive-surge-of-trojanorders-attacks/
